Barracuda’s Report on the Growing Phishing Attacks
Cybercriminals are evolving their tactics at an alarming rate. In the first two months of 2025, Barracuda’s security systems blocked over a million phishing attempts originating from Phishing-as-a-Service (PhaaS) platforms. The report sheds light on the growing sophistication of these attacks, making them harder to detect and more damaging for businesses and individuals.
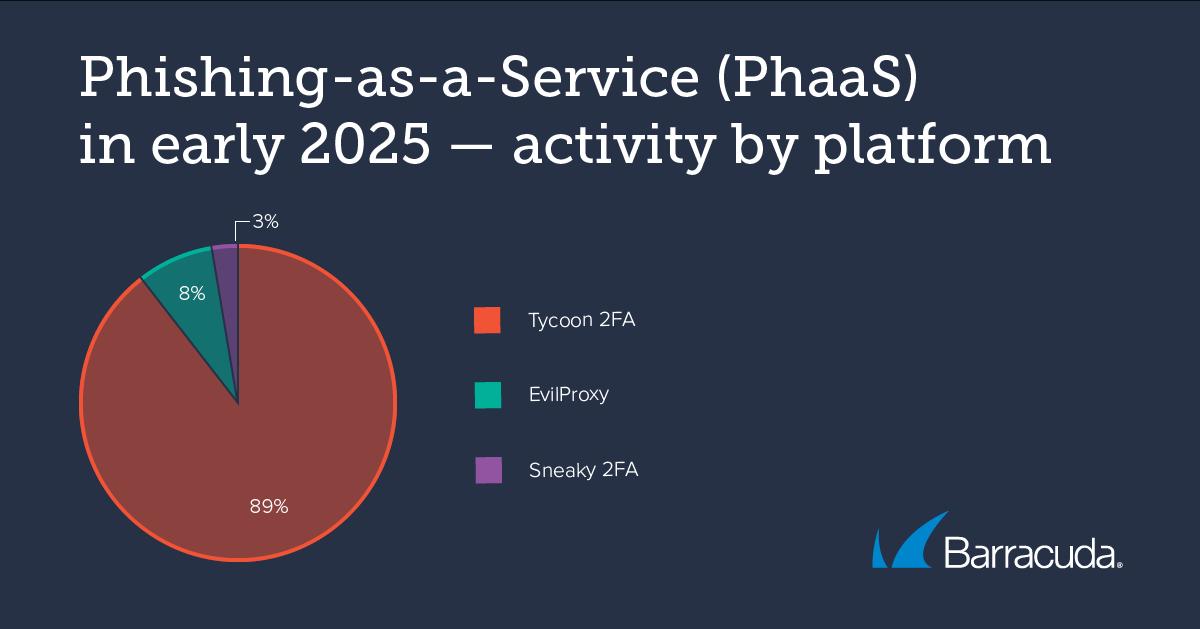
The report of Barracuda highlights that many of these attacks targeted users of popular cloud-based services, especially Microsoft 365. The leading PhaaS platforms behind these incidents included Tycoon 2FA, EvilProxy, and a newcomer, Sneaky 2FA. Each of these platforms uses advanced techniques to bypass security measures and steal sensitive information.
Tycoon 2FA: The Most Advanced PhaaS Platform
As per Barracuda’s report, Tycoon 2FA led the attack landscape, accounting for 89% of detected incidents. This platform constantly evolves, using advanced evasion techniques to bypass traditional security defenses.
One of its most dangerous upgrades is the encryption and obfuscation of its credential theft scripts. Attackers use substitution ciphers and hidden characters, such as the Hangul Filler, to mask their malicious code. Additionally, Tycoon 2FA can detect a victim’s browser type and customize attacks accordingly.
Another concerning feature is its integration with the messaging app Telegram. Barracuda report suggests that cybercriminals use this platform to exfiltrate stolen credentials in real time. By encrypting stolen data with AES encryption before sending it to remote servers, Tycoon 2FA makes detection even more challenging for security tools.
EvilProxy: A Phishing Tool for Everyone
EvilProxy, responsible for 8% of phishing attacks, is particularly concerning due to its accessibility. Unlike highly technical hacking tools, EvilProxy allows even novice cybercriminals to execute sophisticated attacks.
The phishing pages generated by EvilProxy closely mimic real login pages from Microsoft 365, Google, and other cloud services. These fake sites are nearly indistinguishable from legitimate ones, making it easier to trick users into entering their credentials. Once stolen, these credentials can be used to compromise accounts, steal sensitive data, and even launch further attacks.
Sneaky 2FA: A New Player with Smart Tricks
Sneaky 2FA, responsible for 3% of phishing incidents, is a newer but equally dangerous threat found in the Barracuda report. It specializes in adversary-in-the-middle (AiTM) attacks, targeting Microsoft 365 users. Like Tycoon 2FA, it relies on Telegram to manage stolen credentials.
One of its unique capabilities is its ability to identify whether a potential victim is a real user or a security tool. If it detects a bot or an automated security scan, it redirects them to a harmless website, avoiding detection. It also exploits Microsoft 365’s ‘autograb’ functionality, pre-filling fake phishing pages with a user’s email address to make the attack appear more legitimate.
A Growing Concern for Businesses and Individuals
Phishing attacks have become more sophisticated, with PhaaS platforms making it easier for cybercriminals to launch highly targeted campaigns. As security tools advance, so do these malicious platforms, constantly upgrading their techniques to evade detection.
Barracuda security expert Saravanan Mohankumar warns, “The platforms that power phishing-as-a-service are increasingly complex and evasive, making phishing attacks both harder for traditional security tools to detect and more powerful in terms of the damage they can do. An advanced, multilayered defense strategy with AI/ML-enabled detection, combined with a strong security culture and consistent security access and authentication policies, will help to protect organizations and employees against PhaaS-based attacks.”
How to Stay Protected Against Phishing Attacks
The Barracuda report also suggests that with phishing threats evolving rapidly, businesses and individuals must adopt proactive security measures. Here are a few best practices to stay safe:
- Enable Multi-Factor Authentication (MFA): Even if credentials are stolen, MFA adds an extra layer of security.
- Be Cautious of Unexpected Emails: Avoid clicking on links or downloading attachments from unknown senders.
- Verify Login Pages: Always check URLs before entering credentials, especially for cloud-based services.
- Use AI-Powered Security Solutions: Advanced security tools that leverage artificial intelligence can help detect and block phishing attempts more effectively.
- Educate Employees and Users: Regular security training can reduce the likelihood of falling for phishing scams.
Final Thoughts
The rise of PhaaS platforms like Tycoon 2FA, EvilProxy, and Sneaky 2FA highlights the need for stronger cybersecurity measures. These platforms continuously evolve, making traditional security tools less effective. Businesses and individuals must stay informed, implement multi-layered security strategies, and remain vigilant against phishing threats. With the right defenses in place, it is possible to reduce the risk of falling victim to these highly sophisticated attacks.
